Living in a digital world offers convenience for managing your finances, but it also exposes you to evolving cyber threats. From phishing scams and ransomware to AI-powered deepfakes, cybercriminals are constantly finding new ways to target your money and identity. Here’s how you can protect yourself:
- Use Multi-Factor Authentication (MFA): Add extra layers of security to your accounts with authenticator apps or hardware security keys.
- Encrypt Your Data: Secure your devices and communications with tools like full-disk encryption and end-to-end encrypted apps.
- Practice Safe Online Banking: Avoid public Wi-Fi, enable transaction alerts, and always log out after accessing accounts.
- Monitor Accounts Regularly: Check statements weekly and set up real-time alerts to catch suspicious activity early.
- Prepare for Ransomware: Follow the 3-2-1 backup rule to safeguard critical financial data.
Cybercrime is on the rise, with phishing attacks up 1,200% and ransomware costing financial institutions millions annually. Protecting your finances requires a mix of strong authentication, encryption, and safe online habits. Start taking these steps today to stay ahead of threats.
Common Cyber Threats Targeting Your Finances
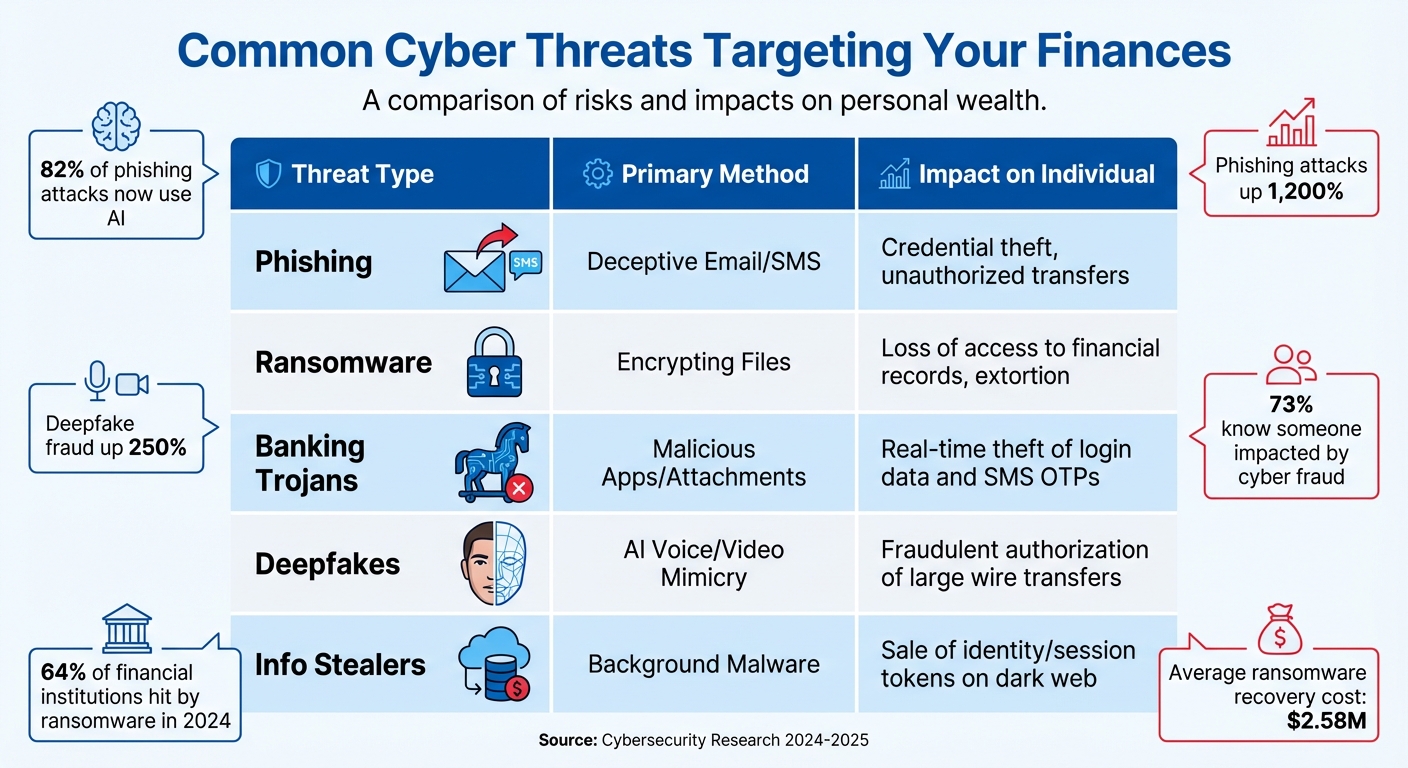
The financial sector has long been a prime target for cybercriminals. In fact, nearly 20% of all cyberattacks in the past two decades have been aimed at financial institutions and their customers. These attacks aren’t just alarming – they’re costly. The average cost of a data breach in the financial sector is $6.08 million, which is 22% higher than the global average.
To protect your finances, it’s essential to understand the threats you face. Let’s break down some of the most common and emerging risks that could jeopardize your financial security.
Phishing, Identity Theft, and Ransomware
Phishing scams use fake emails or text messages (often referred to as "smishing") to trick you into sharing sensitive information like passwords, account numbers, or Social Security details. These attacks are becoming more sophisticated, with 82% now incorporating AI, making them harder to spot. Phishing attacks have skyrocketed – up by nearly 1,200% since the rise of AI tools.
Identity theft takes things a step further. Cybercriminals use stolen personal data to open fraudulent credit accounts, withdraw money from your accounts, or even take out loans in your name. One particularly tricky form of this is synthetic identity theft, where real personal data is mixed with fake details to create fraudulent identities. These fake accounts can fly under the radar for months, making them extremely difficult to detect.
Ransomware is another growing threat. It locks you out of your financial files or accounts until you pay a ransom. In 2024, 64% of financial institutions experienced a ransomware attack, with recovery costs averaging $2.58 million.
Other stealthy tools like banking Trojans and information stealers pose additional risks:
- Banking Trojans are designed to steal your financial credentials. For example, in July 2025, the Anatsa (Teabot) Banking Trojan – disguised as a harmless PDF app – infected 90,000 users and targeted over 831 financial institutions. It used fake login screens to capture credentials in real-time.
- Information stealers silently collect browser cookies, saved passwords, and session tokens. In May 2025, Bitsight, working with the FBI and Microsoft, disrupted the Lumma Stealer malware, which had infected nearly 400,000 devices globally to harvest financial data. This stolen information is often sold on the dark web, enabling delayed account takeovers.
Third-Party Vulnerabilities
Sometimes, your financial data isn’t compromised through your own actions but through breaches at third-party vendors. For instance, in February 2024, Bank of America alerted 57,000 customers that sensitive data, including Social Security numbers and passwords, had been leaked due to a ransomware attack on their vendor Infosys McCamish Systems. Similarly, in May 2024, a breach at a vendor for Santander Bank exposed sensitive data for over 30 million customers.
New Threats: Deepfakes, Vishing, and Social Engineering
Advances in artificial intelligence have opened the door to entirely new types of cyber threats.
Deepfakes use AI to create convincing fake voices or videos, often impersonating bank officials or family members to authorize fraudulent transactions. These attacks are highly effective because they exploit your trust in familiar faces or voices. Deepfake-related fraud targeting banks rose by nearly 250% last year.
Vishing (voice phishing) involves real-time phone scams where attackers pose as representatives from financial institutions or government agencies to extract sensitive information. These calls are designed to create a sense of urgency, pressuring victims into quick decisions. Wealthy individuals are often targeted through social engineering, where attackers research their victims extensively before making contact.
AI is making these attacks more dangerous than ever. Over the past year, 45% of financial organizations reported being targeted by AI-powered cyberattacks. Platforms like "SpamGPT" now allow criminals to launch highly convincing phishing campaigns at scale. According to a 2026 survey, 87% of cybersecurity experts identified AI vulnerabilities as the fastest-growing cyber risk in 2025, with 94% predicting that AI will significantly reshape the cyber threat landscape in 2026.
The personal toll is immense. In 2025, 73% of individuals reported knowing someone impacted by cyber fraud. These are real people – friends, family, and colleagues – who’ve lost savings, struggled with identity theft, or spent months recovering from financial fraud.
| Threat Type | Primary Method | Impact on Individual |
|---|---|---|
| Phishing | Deceptive Email/SMS | Credential theft, unauthorized transfers |
| Ransomware | Encrypting Files | Loss of access to financial records, extortion |
| Banking Trojans | Malicious Apps/Attachments | Real-time theft of login data and SMS OTPs |
| Deepfakes | AI Voice/Video Mimicry | Fraudulent authorization of large wire transfers |
| Info Stealers | Background Malware | Sale of identity/session tokens on dark web |
Understanding these threats is the first step toward safeguarding your financial well-being. With this knowledge, you can focus on implementing stronger authentication measures and encryption to protect your assets.
sbb-itb-39d39a6
Setting Up Strong Authentication for Financial Accounts
Now that you’re aware of the risks, it’s time to secure your accounts with authentication methods that truly work. Adding layers of authentication can help keep unauthorized users out of your financial accounts.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA), often referred to as two-factor authentication (2FA), requires you to verify your identity using two or more different factors before gaining access to an account. As the Federal Trade Commission explains:
"Using two-factor authentication is like using two locks on your door – and is much more secure."
MFA works by combining factors you know (like a password), have (like a smartphone or security key), or are (like a fingerprint). By activating MFA, even if someone manages to steal your password, they can’t log in without the second layer of verification, which is much harder to compromise.
Focus on enabling MFA for your most sensitive accounts, such as banking apps, investment platforms, your primary email (used for password resets), and tax filing services. However, not all MFA methods offer the same level of protection. Codes sent via SMS or email can be vulnerable to attacks like SIM-swapping or email breaches. For better security, use an authenticator app (like Google Authenticator or Microsoft Authenticator) or, for the highest level of protection, a hardware security key such as YubiKey or another FIDO2-compliant device. These physical keys rely on encryption and require your physical presence, making them nearly impossible to hack remotely.
Avoid logging into sensitive accounts on public computers, as they may store credentials or be compromised. Additionally, set up transaction and account change alerts via text or email from your financial institutions. These notifications can help you detect unauthorized activity quickly.
| MFA Method | Security Level | Pros | Cons |
|---|---|---|---|
| SMS / Email Codes | Basic | Easy to use; no extra hardware needed. | Vulnerable to SIM-swapping and email breaches. |
| Authenticator Apps | Enhanced | Resistant to SIM-swapping; provides push notifications. | Requires a smartphone; codes can be lost without backups. |
| Security Keys | Strongest | Uses encryption; physical possession required; immune to remote theft. | Requires purchasing a device; can be lost or misplaced. |
While MFA is a powerful tool, it works best when paired with strong password practices.
Password Management Tools
A reliable password manager is essential for generating and storing unique, strong passwords for every account. Protect your password manager with MFA to guard against credential stuffing and potential breaches. Your master password – the one you’ll need to remember – should be both strong and memorable. A passphrase made up of four to seven unrelated words (e.g., "HorsePurpleHatRunBay") is a great option. The National Institute of Standards and Technology (NIST) suggests passwords be at least 12 characters long, though many experts recommend 16 or more for financial accounts.
Once you’ve set up your password manager, let it create unique, random passwords for each financial platform. Secure your password vault with MFA – preferably using an authenticator app or a security key – to add an extra layer of protection in case your master password is compromised.
Regularly review your passwords using your manager’s built-in tools to identify weak, outdated, or reused credentials. Never reuse usernames or passwords across multiple accounts. If security questions are required, treat them like passwords – use long, random strings instead of easily guessed personal details.
Finally, only enter your password manager credentials on secure websites that start with "https://". Double-check the site’s security certificate by clicking the padlock icon in your browser. This quick step can help you avoid phishing sites designed to steal your master password. These precautions are crucial for keeping your financial data and transactions safe.
Using Encryption to Protect Financial Data
Strong passwords and multi-factor authentication (MFA) are essential for securing access to your accounts, but encryption takes protection a step further by safeguarding the actual data itself. Whether stored on your devices or traveling across the internet, encryption scrambles financial information into an unreadable format that only someone with the correct key can decode.
And the stakes? They’re enormous. By 2025, the global average cost of a data breach reached USD 4.44 million. However, organizations using encryption can cut that financial damage by over USD 200,000. As IBM aptly puts it:
"Encryption is often the first and last defense against hackers and data breaches."
For anyone managing their finances online, encryption isn’t just a nice-to-have – it’s an essential layer of protection. It works hand-in-hand with authentication strategies to create a comprehensive shield for your financial data.
File and Full-Disk Encryption
Encrypting your devices ensures that even if they’re lost or stolen, your financial records remain secure. Full-disk encryption automatically protects everything on your device, while file and folder encryption lets you focus on securing specific sensitive documents, like tax returns or investment statements.
The Advanced Encryption Standard (AES) is widely regarded as the benchmark for encryption, offering key lengths of 128, 192, or 256 bits. The longer the key, the tougher it is to crack. Many modern devices already come with built-in encryption tools:
- Windows: Use BitLocker to enable full-disk encryption.
- macOS: Turn on FileVault in Security & Privacy settings.
- Linux: LUKS provides reliable encryption options.
For cross-platform needs, VeraCrypt is a trusted open-source tool that allows you to create encrypted containers for specific files. Just remember: when setting up encryption, you’ll receive a recovery key. Store this key somewhere safe, because losing it means you may permanently lose access to your data.
When it comes to backups, always use encrypted storage devices or cloud services that encrypt data at rest. And don’t forget to check that your cloud provider also supports MFA for added security.
Secure Communication Channels
Encryption isn’t just about protecting stored data – it’s equally critical for securing data in transit. Sharing sensitive financial information, like account numbers or tax documents, requires secure communication channels. Standard email and text messages often lack end-to-end encryption (E2EE), leaving your data vulnerable to interception. E2EE ensures that your information is encrypted on your device and can only be decrypted by the intended recipient.
Apps like Signal, which grew its user base from 12 million to 40 million in 2022, are excellent for secure communications. Signal encrypts messages, voice calls, video calls, and even file attachments, making it a solid choice for sharing sensitive financial details. Other popular platforms, such as WhatsApp and iMessage, also offer E2EE by default.
Encryption also plays a role in securing web traffic. Look for the "https://" in website URLs – it’s a sign that the connection is encrypted and secure. As the Federal Trade Commission explains:
"The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely."
Public Wi-Fi networks, like those in cafes or airports, are often poorly secured. Avoid conducting financial transactions on these networks. If remote access is unavoidable, use your cellular data or a Virtual Private Network (VPN) to create a secure, encrypted tunnel for your internet traffic.
However, it’s important to note that encryption has its limits. While apps with E2EE protect data during transmission, they don’t secure unencrypted copies stored on your device. As the Electronic Frontier Foundation warns:
"Using an encrypted chat app to share personal photos won’t protect the confidentiality of those photos if you store unencrypted copies on your laptop and your laptop is stolen."
To fully protect your financial data, combine communication encryption with device encryption. And always log out of financial accounts after use – not just by closing your browser, but through the proper log-out process – to avoid session hijacking. If you ever receive an urgent request for financial information, even over an encrypted channel, confirm the source by independently contacting them through a verified number.
Safe Online Banking and Transaction Monitoring
Strong authentication and encryption are essential for protecting your finances, but your online banking habits play an equally critical role. The FBI’s Internet Crime Complaint Center reported over 5,100 account-takeover complaints since early 2025, with losses surpassing $262 million. Additionally, about 14% of consumers have fallen victim to digital scams. The good news? Many of these attacks can be avoided with smart browsing practices and diligent account monitoring.
Safe Browsing Habits
When logging into your bank account online, always check for "https://" in the web address. As the FDIC points out:
"The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely."
Avoid clicking on links from emails, texts, or ads, even if they appear to come from your bank. Scammers often use deceptive ads or phishing messages to trick users. Instead, type your bank’s URL directly into your browser or use the official mobile app.
Public Wi-Fi networks, like those in cafes or airports, are often unsecured, making them a risky choice for online banking. Stick to your home network or cellular data for secure access. If you must use public Wi-Fi, connect through a Virtual Private Network (VPN) to protect your data with encryption. At home, ensure your Wi-Fi is secured with WPA2 or WPA3 encryption and a unique password.
To stay ahead of potential threats, enable real-time transaction alerts through your bank’s app or website. These notifications can quickly alert you to unauthorized activity. Also, make it a habit to log out of your banking session to prevent session hijacking. Safe browsing is your first line of defense, but ongoing account monitoring is equally important.
Monitoring and Detecting Unusual Activity
Secure browsing is only part of the equation. Actively monitoring your accounts is just as crucial. Review your bank and credit card statements weekly to spot any unusual activity or unauthorized charges.
The U.S. Department of Labor highlights the importance of registering for online accounts:
"Failing to register for an online account may enable cybercriminals to assume your online identity."
Make sure to enable online access for all your financial accounts, including retirement, HSA, and investment accounts, to prevent unauthorized registrations. Additionally, take advantage of your right to free annual credit reports from the three major credit bureaus. These reports can help you identify unfamiliar accounts or creditors. In 2025, over 1 million identity theft cases were reported to the Federal Trade Commission. If you notice anything suspicious, act immediately: contact your financial institution, update your account passwords, and place a fraud alert with the credit bureaus. You can also report incidents through IdentityTheft.gov or the FBI’s Internet Crime Complaint Center.
Be mindful of advanced threats like Automatic Transfer Systems (ATS). This malware can execute unauthorized transfers during your banking session without your knowledge. Regularly checking your account balances can help you catch these fraudulent activities early.
Preparing for and Recovering from Ransomware Attacks
Even with the best security tools in place, ransomware attacks remain a persistent danger. The real secret to minimizing the fallout isn’t just about prevention – it’s having a reliable backup and recovery plan. Ransomware works by encrypting your files, making them inaccessible, and often targets your backups to ensure you can’t restore your data without paying the ransom. The Cybersecurity and Infrastructure Security Agency (CISA) stresses:
"It is important that backups are maintained offline, as many ransomware variants attempt to find and subsequently delete or encrypt accessible backups to make restoration impossible unless the ransom is paid."
By keeping backups offline, you can recover your financial records without giving in to ransom demands. But it’s not just about having backups – it’s about following a tested protocol to ensure they’re effective when you need them most.
The 3-2-1 Backup Rule
The 3-2-1 backup rule is a time-tested strategy: keep three copies of your data, store them on two different types of media, and ensure one copy is offline. For example, you might store your data on your computer’s hard drive and an external USB drive, with one of those backups kept offline.
If you’re backing up sensitive documents like tax returns, bank statements, or cryptocurrency wallet information to an external hard drive, disconnect the drive immediately after the backup is complete. This simple step ensures ransomware can’t access the backup, even if your main system is compromised.
Some cloud storage providers also offer immutable storage, which prevents files from being altered or deleted for a set period. While this can be a strong safeguard, it’s essential to configure it correctly to avoid unexpected charges.
For those managing more complex financial systems, consider maintaining "golden images" – preconfigured snapshots of your operating system and essential software. These templates allow you to quickly rebuild your system on a clean network after an attack. Additionally, keeping spare hardware on hand can save critical time during restoration.
Testing Your Recovery Process
Creating backups is just the first step. You need to ensure they work when it matters most. CISA advises:
"If your computer becomes infected with ransomware, you can restore your system to its previous state using your backups."
To ensure your backups are reliable, test them quarterly. Restore specific files, such as tax records or investment documents, and check that they open correctly and are complete. Always scan backups with updated antivirus software before restoring them, as dormant malware could be lurking.
Track how long the restoration process takes, so you’re prepared for the timeline during a real incident. Keep a hard copy of your recovery checklist and critical account details in a secure place, as ransomware could lock you out of digital versions. For added safety, test your backups on an isolated network or a separate device. Regular testing not only ensures your backups are functional but also strengthens your overall preparedness for ransomware threats.
How Global Wealth Protection Enhances Financial Security
Protecting financial assets in today’s digital age requires more than just cybersecurity tools. While these tools are essential, they’re not enough on their own. A comprehensive defense strategy needs to combine strong digital security measures with legal structures that add extra layers of protection. As Steven J. Ursillo, Jr., Partner at Cherry Bekaert, puts it:
"It is vital that organizations understand that the threat to their digital assets can come from every area of their system and application environment – then develop a defense in depth strategy to match."
This approach isn’t just for businesses; it’s equally important for individuals managing substantial wealth. By integrating legal frameworks with digital safeguards, you create a multi-layered defense system. Global Wealth Protection takes this concept further, offering tools like offshore trusts, private US LLCs, and secure asset transfer strategies to protect global entrepreneurs and high-net-worth individuals.
Offshore Trusts and Private US LLCs
Offshore trusts and private US LLCs serve as powerful tools to shield assets. These legal structures create privacy and legal barriers, separating your identity from your wealth. For example, if cybercriminals target your financial accounts, assets held in an offshore trust or private LLC are harder to access directly. This added layer of complexity can deter potential threats.
Another advantage is the ability to leverage data sovereignty. With cybercrime costs projected to hit $23.84 trillion annually by 2027, and 83% of attacks originating outside traditional security boundaries, placing assets in jurisdictions with robust privacy laws can reduce risk. For instance, even if a U.S.-based institution experiences a data breach, assets stored in an offshore trust – such as one in Anguilla – remain protected and out of immediate reach.
Additionally, spreading wealth across multiple legal entities can aid in asset recovery. If one account is compromised, having assets distributed gives you time to respond, freeze access, and recover funds without losing everything.
Consultations for Secure Digital Asset Transfers
Managing digital assets requires a specialized approach. Since 2012, cybercriminals have stolen $2.72 billion from exchanges, highlighting the need for advanced strategies. Global Wealth Protection offers personalized consultations to help clients develop secure methods for transferring and managing assets across platforms and borders.
These consultations focus on practical, actionable steps, such as using asset segregation. For instance, funds can be divided between "hot" online wallets for daily transactions and "cold" offline wallets for long-term storage. They also guide clients in adopting zero-trust security models and hash-based verification systems to ensure data integrity. For those with complex portfolios, consultations include setting spending limits, verifying large transactions, and establishing secure channels to transfer funds while minimizing risks.
Whether you’re a digital nomad navigating income streams across different countries or a high-net-worth individual safeguarding generational wealth, these tailored consultations ensure your strategies align with both cybersecurity measures and legal protections. By combining personalized advice with robust legal structures, Global Wealth Protection provides a strong, comprehensive defense for your financial assets in an increasingly digital world.
Conclusion
This guide blends technical defenses with legal strategies to help create a strong framework for protecting your assets. Safeguarding your wealth is not just important – it’s essential.
Start with multi-factor authentication (MFA) and strong, unique passwords that are 12–15 characters long. As FINRA highlights:
"Enabling multifactor authentication (MFA) can significantly reduce the likelihood of a cybercriminal taking over your account".
Encryption is another key tool to keep your data secure. Pair it with regular updates, backups, and consistent monitoring to close off vulnerabilities and detect fraud early. Real-time alerts for transactions, password changes, and login attempts add an extra layer of protection. And don’t underestimate the risks of social engineering. From AI-powered deepfakes to impostor scams, staying vigilant is critical. The FDIC recommends:
"A safe strategy is to ignore unsolicited requests for information, no matter how legitimate they appear, especially if they ask for information such as a Social Security number, bank account numbers and passwords".
Beyond digital safeguards, professional services and legal structures can add extra layers of defense. Offshore trusts, for instance, can help with asset segregation, while consulting specialists ensures secure handling of digital asset transfers. These measures create significant hurdles for potential threats.
Take action now: enable MFA, use a password manager, secure your online accounts, and set up transaction alerts. The risks to your financial assets are real and evolving, but with the right precautions, you can stay ahead of cybercriminals and keep your wealth secure.
FAQs
What steps can I take to protect my financial accounts from phishing and identity theft?
Protecting your financial accounts from phishing and identity theft starts with creating strong and unique passwords or passphrases for every account. A password manager can be a game-changer here, helping you securely store and organize them all. Another must? Turn on multi-factor authentication (MFA) wherever it’s offered – it’s like adding a second lock to your door.
Be mindful of where and how you share personal or financial information online. Avoid clicking on links or downloading attachments from emails or messages you weren’t expecting – these are common tricks used in phishing scams. When entering sensitive details, stick to secure websites (look for "https" in the URL). And don’t forget to keep an eye on your accounts for anything that looks odd. If you spot something unusual, notify your bank or financial institution right away.
Staying alert and making these practices part of your routine can go a long way in protecting you from cyber threats.
How does encryption help protect my financial information?
Encryption is an effective way to shield your financial information. It works by transforming sensitive data – like bank account details or transaction records – into a format that’s unreadable without proper authorization. This means that even if someone intercepts the data, they won’t be able to understand or misuse it. It’s crucial for activities like online banking or handling finances on digital platforms.
By encrypting your information, you can lower the chances of identity theft, fraud, or financial loss. It also reduces the damage that a data breach might cause, offering an added layer of protection. In today’s digital age, encryption is a must-have for anyone managing their finances online, ensuring personal and financial details remain secure.
Why is multi-factor authentication important for securing online banking?
Multi-factor authentication (MFA) plays a critical role in securing online banking. It goes beyond the basic username and password by adding an extra layer of verification, such as a one-time code sent to your phone or email. This extra step ensures that even if someone manages to steal your password, they can’t access your account without that second piece of information.
By requiring multiple forms of authentication, MFA dramatically lowers the chances of unauthorized access, account takeovers, and financial fraud. In a world where cyber threats are constantly evolving, this added security measure helps protect your personal information and financial assets from falling into the wrong hands.

